Get insights.
Unlock value.
- Free plan, no time limit
- Set up in minutes
- No credit card required
How to Collect Verified Crypto Wallet Addresses for Whitelists, Allowlists, Waitlists, and Airdrops
Introduction
In today's digital landscape, identity verification is essential to ensure secure and trustworthy online transactions and interactions. With the rise of decentralized technologies like blockchain, Web 3.0 wallets power decentralized identities. But, there is no way to collect verified identities, thus a lack of trust in the data that is being collected. Here is how it looks today: most of the time, Web 3.0 companies use Web 2.0 forms & surveys to collect data. e.g., if you are creating a whitelist, Web 3.0 users are asked to copy and paste their wallet addresses into forms like Typeform and Google Forms. This process is error-prone, cumbersome, and doesn't validate the identity. This is a big problem for Web 3.0 companies.
In this guide, we will show you a step-by-step guide on how to use BlockSurvey to collect verified Web 3 identities for whitelist, waitlist, and airdrop registration, to name a few. Read further.
A Step-By-Step Guide to Using BlockSurvey for Web 3.0 Wallet Addresses
Step 1: Add a Web 3 Identity Verification component
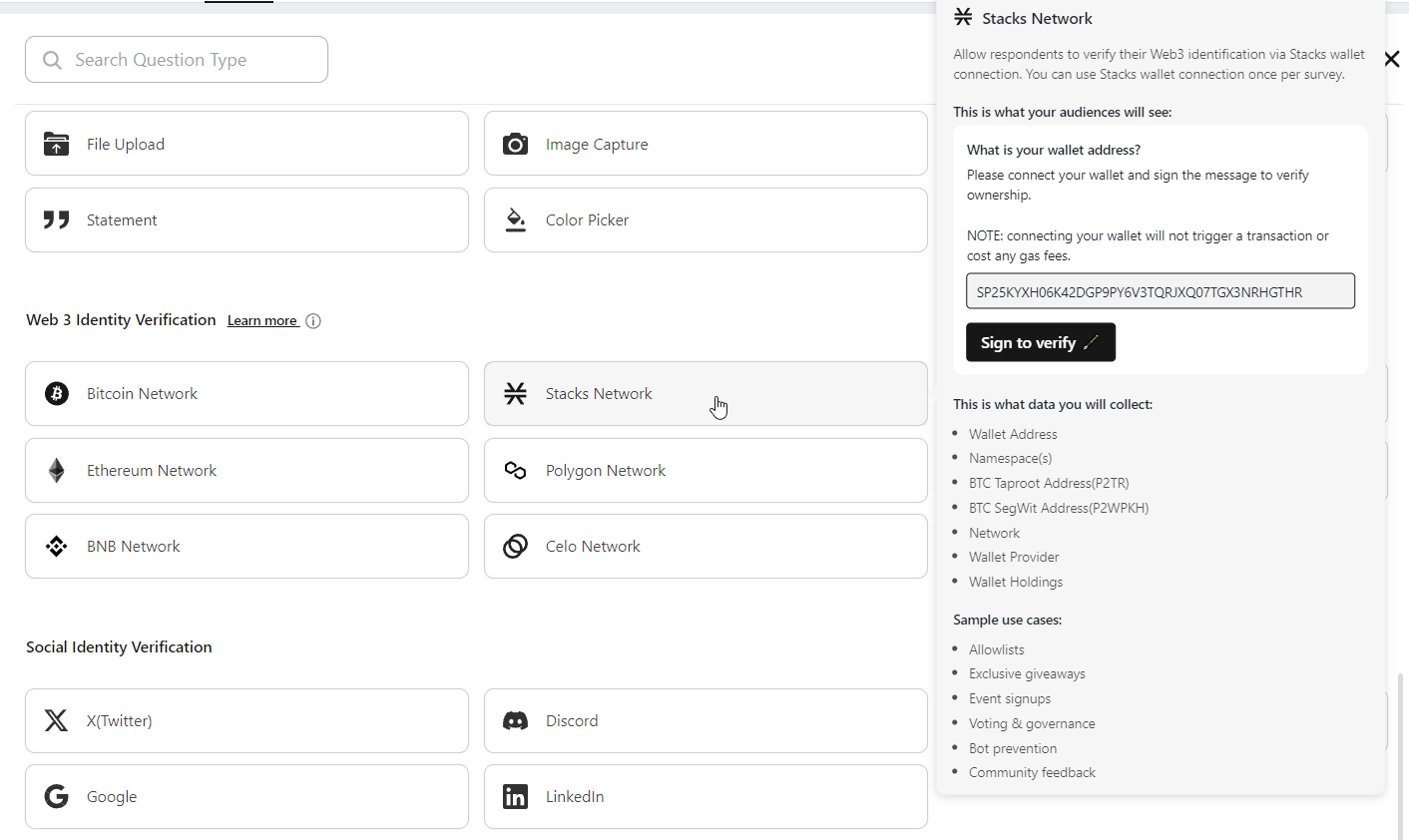
If you're an existing member, navigate to Design Builder and click on the 'Add Question by Type' button. In the list of categories, find the 'Web 3.0 Identity Verification' component. Here, you'll see all the blockchain networks supported for verifying user identities.
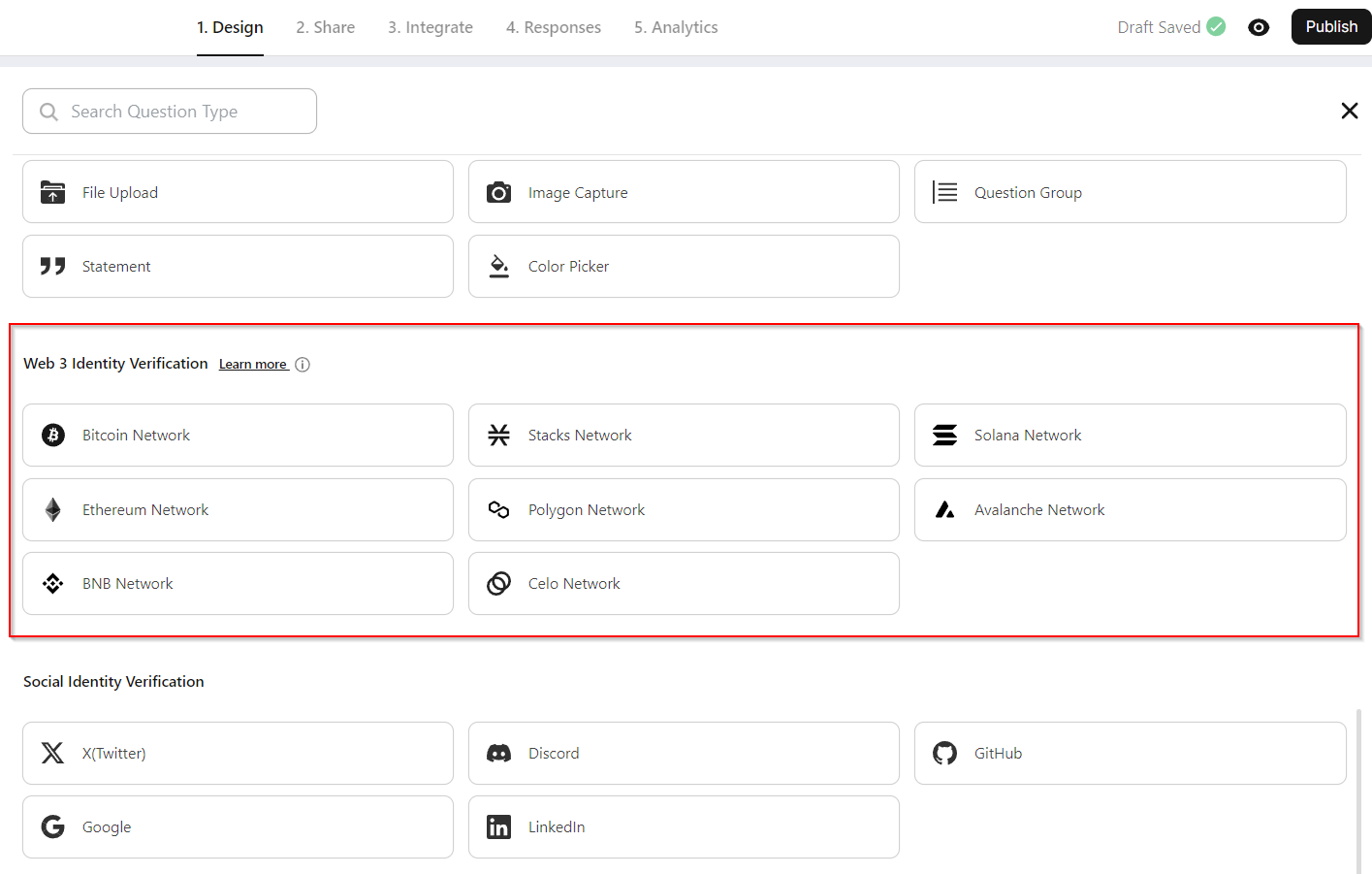
Step 2: Select a Blockchain Network
BlockSurvey currently supports major blockchain networks such as Stacks, Bitcoin, Solana, Ethereum, Polygon, etc. For a seamless identity verification experience across networks, several wallets, such as Brave Wallet, Leather Wallet, Xverse Wallet, MetaMask, Phantom Wallet, Wallet Connect, and Coinbase Wallet, have been integrated. Choose the desired network where you want to collect wallet addresses, and BlockSurvey takes care of the rest. Based on the network, a wallet choice will be presented to your audience, including support for desktop and mobile. Sample screenshot for collecting Bitcoin and Stacks wallet address on Stacks network.
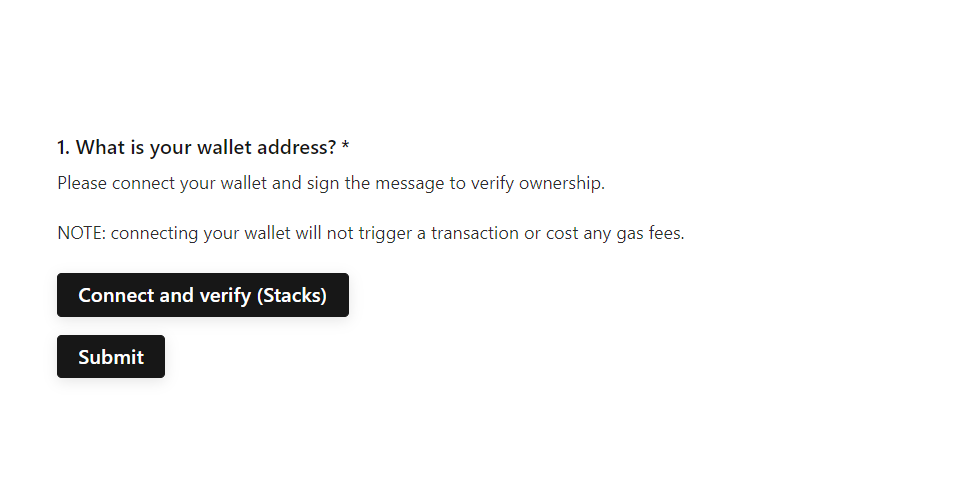
Step 3: Wallet address collection - User Verification Process
Once the BlockSurvey is created, hit Publish and share the URL with your audience. This is how the wallet address collection looks. See screenshot. When the user clicks on the 'Connect and Verify' button, this action will launch the corresponding wallet application to initiate the user's identity verification.
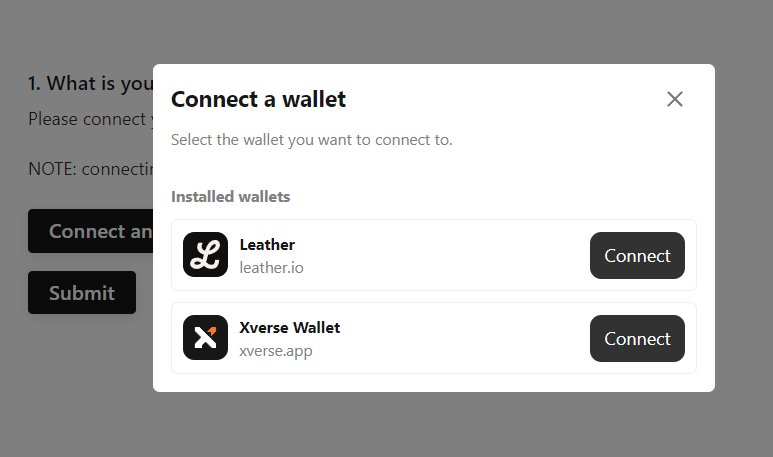
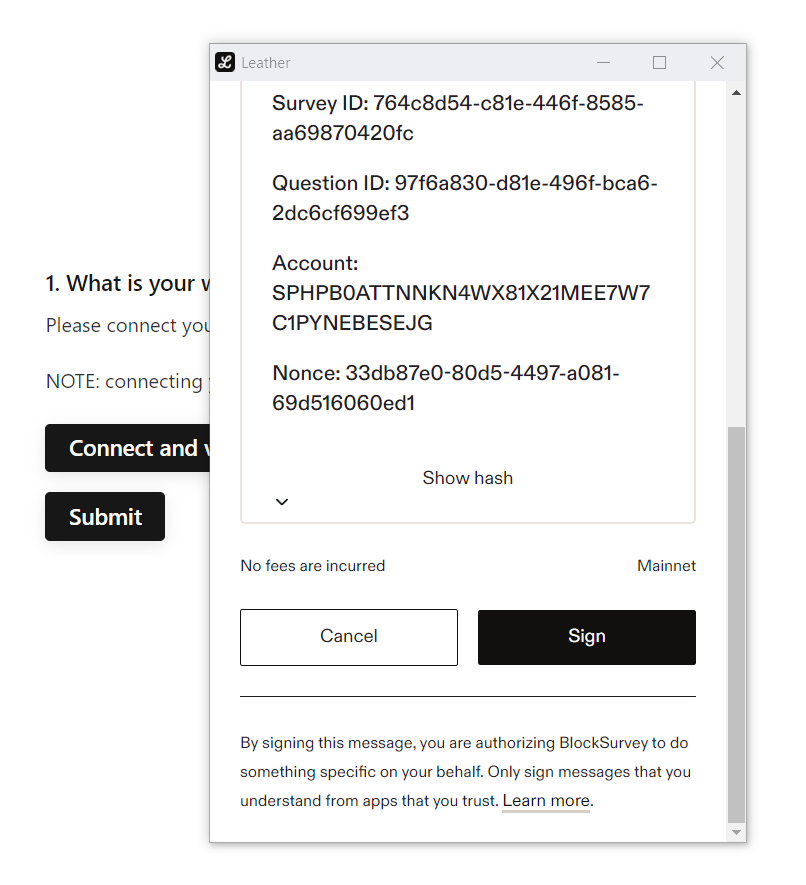
Step 4: Wallet address collection - Account Selection and Message Signing
Users can opt for the account they wish to connect to and proceed to sign a message for identity verification. The system will then retrieve basic public information, such as the wallet address, network provider, decentralized namespaces, and wallet provider utilized for verification.
Step 5: Wallet address collection - Verification Confirmation and Submission
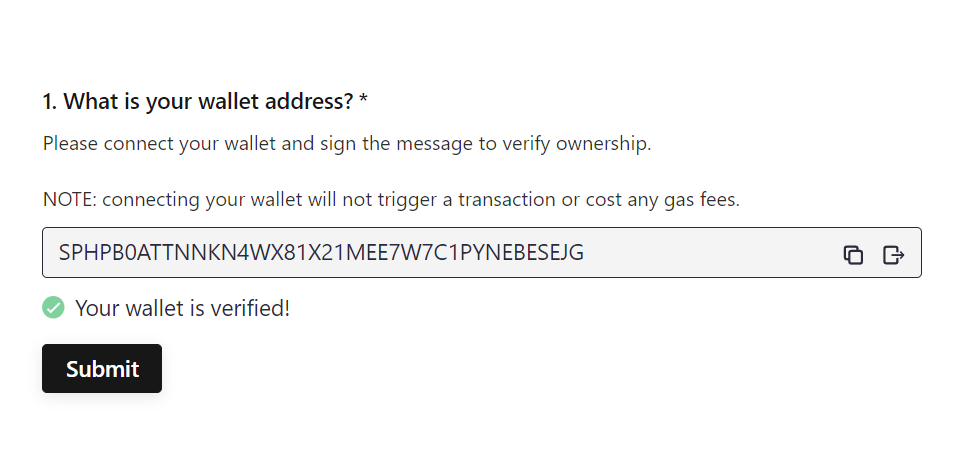
Once the user's identity has been successfully verified, a confirmation message is displayed, as shown below. Note: If the identity verification question is set as required or mandatory, users must complete the verification process prior to submitting the BlockSurvey.
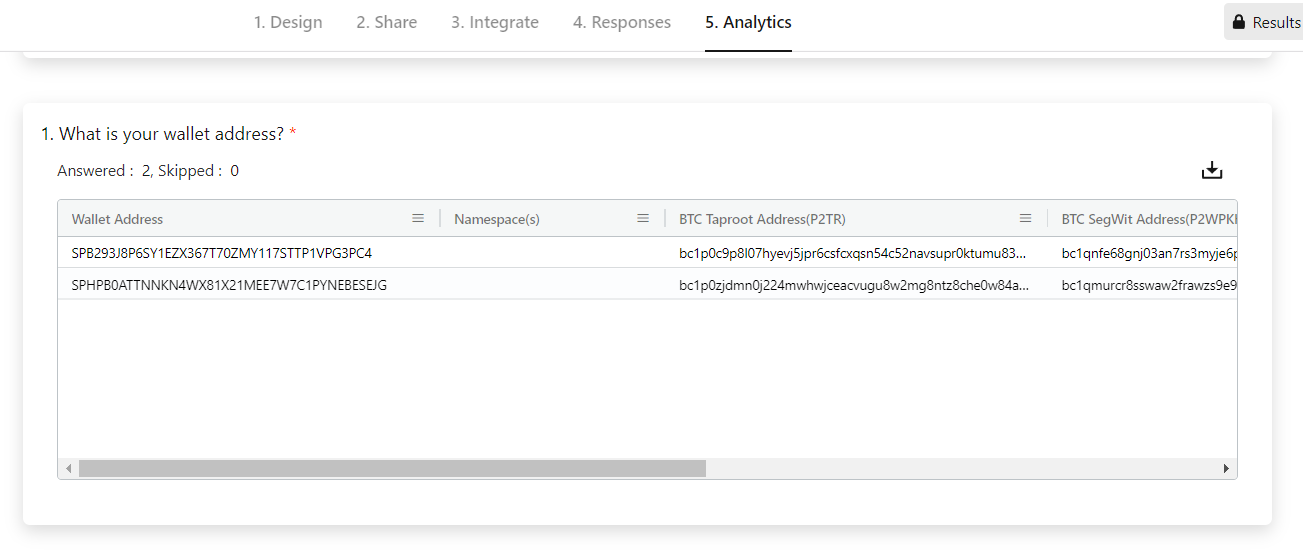
Step 6: View and Analyze the Collected Data
Now that the wallet address has been collected, you can view the data and visualize the data from the BlockSurvey Analytics page. Sample screenshot showing Bitcoin Taproot, Bitcoin Segwit, and Stacks wallet addresses collected from the Stacks Network.
Now that we have seen how you can use BlockSurvey for wallet address collection let's see what are some use-cases you can use it for.
Use cases of each Web3 Identity Verification component
-
Bitcoin Network Identity Identity Verification component and use cases:
Bitcoin Network Identity Verification enhances the transparency and accountability of transactions, fostering a more trusted environment for users engaging in Bitcoin-related activities.
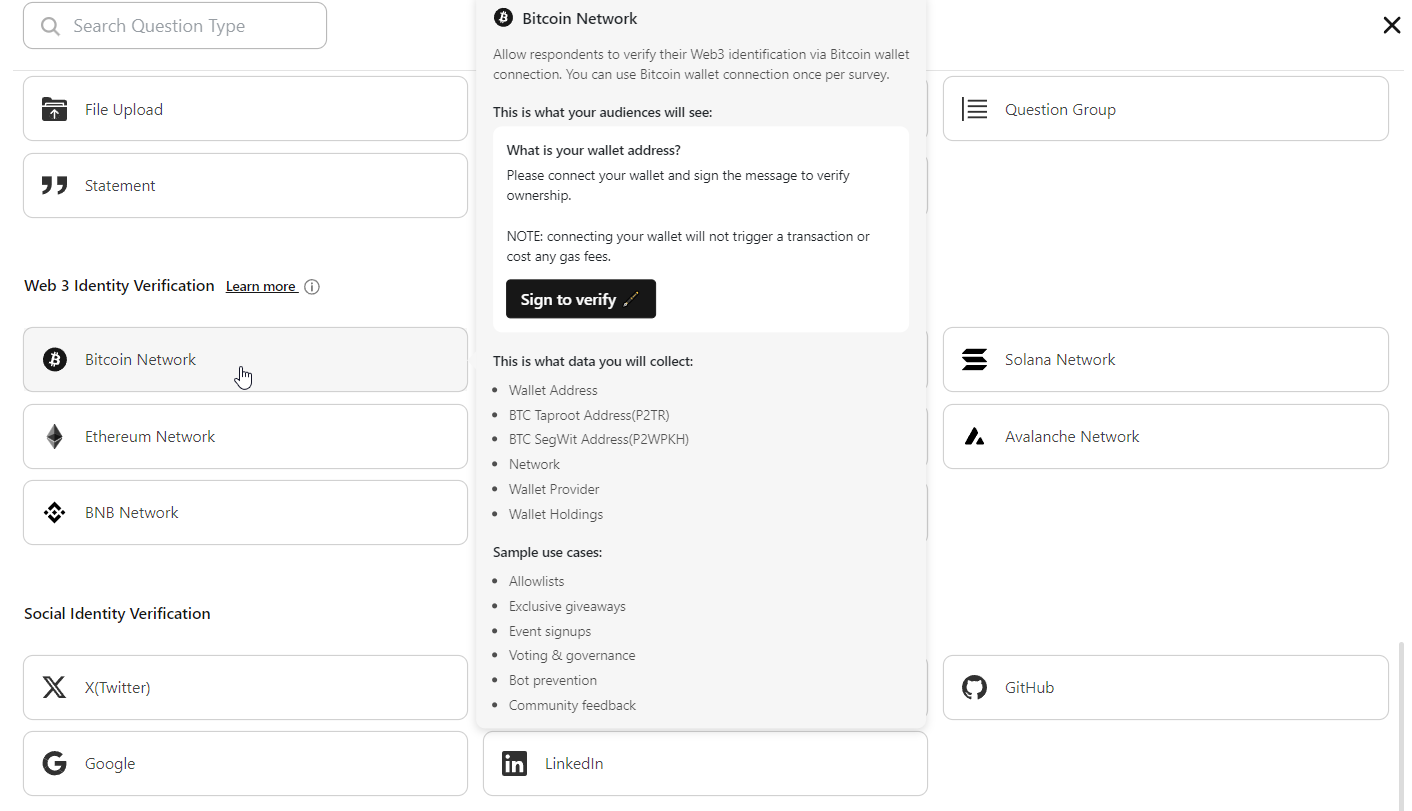
Use cases:
Bot Prevention: BTC Network Identity Verification adds an extra layer of bot prevention by requiring users to verify their identity through their web3 accounts. This method leverages existing Web3 profiles, making it more challenging for bots to infiltrate systems and ensuring a higher level of user authentication.
Exclusive Giveaways: BTC Network Identity Verification involves requiring participants to authenticate their entries through their BTC profiles, enhancing the legitimacy of the engagement. This approach not only adds an extra layer of verification but also fosters a sense of transparency and trust, ensuring that giveaways reach and reward genuine individuals within the community.
-
BNB Network Identity Identity Verification component and use cases:
BNB Identity Verification enhances the transparency and accountability of transactions, fostering a more trusted environment for users engaging in Binance Smart Chain ecosystem activities.
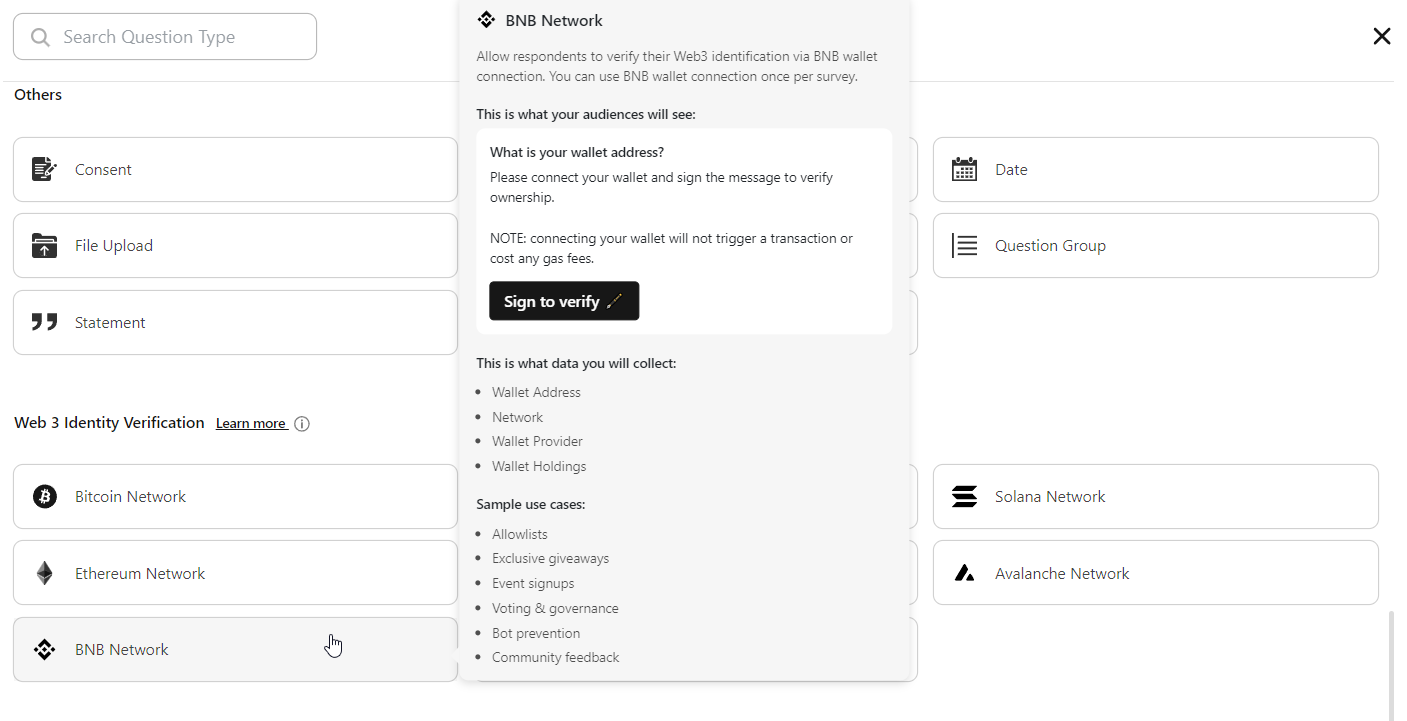
Use cases:
Event Signup Security: BNB Network Identity Verification introduces an additional layer of security for event signups by prompting users to authenticate their identity through their BNB web3 accounts. This approach utilizes established Web3 profiles, heightening the resistance against automated scripts, thereby enhancing the integrity of event signups and ensuring a more authentic and reliable registration process.
Allowlist Management: In the context of allow list management, BNB Network Identity Verification provides an enhanced level of control by requiring users to verify their identity through their web3 accounts. By integrating with existing Web3 profiles, this system fortifies allow list protocols, making it more challenging for unauthorized entities to gain access and ensuring a secure and meticulously managed user allow list.
-
Stacks Network Identity Identity Verification component and use cases:
Stacks Network Identity Verification plays a pivotal role in enhancing security and trust across various use cases, including decentralized finance (DeFi), digital asset management, and decentralized applications (DApps).
Use cases:
Voting and Governance Empowerment: BTC Network Identity Verification plays a pivotal role in ensuring the integrity and transparency of voting and governance processes. By linking user identities to their web3 accounts, this system establishes a secure foundation for democratic decision-making within the network.
Community Feedback Integration: The BTC Network places a high priority on community feedback as an integral part of its development and enhancement strategy. Actively seeking input through surveys, forums, and direct interactions, the network ensures a dynamic and responsive environment.
-
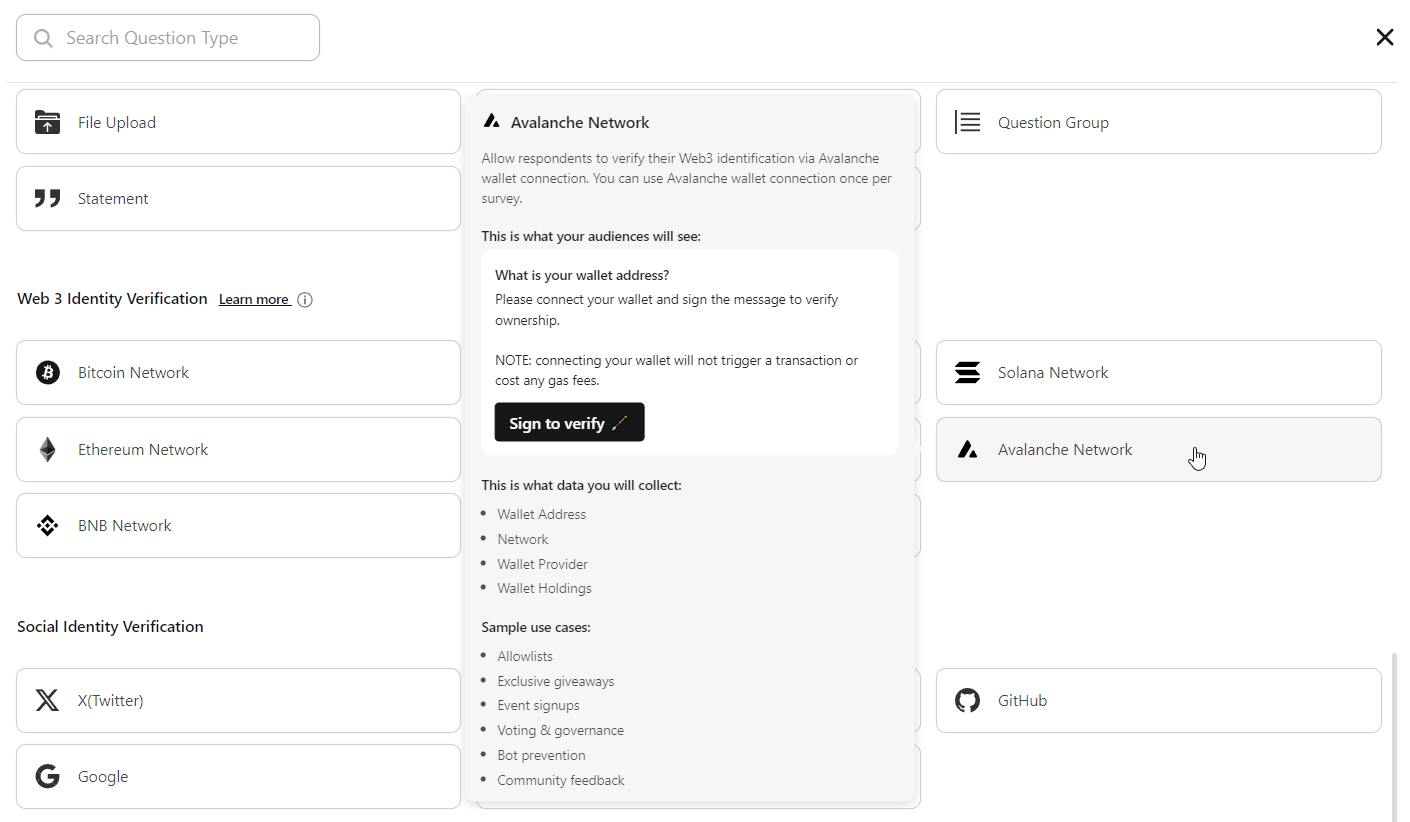
Avalanche Network Identity Identity Verification component and use cases:
Avalanche Network Identity Verification component facilitates trust and integrity across a spectrum of applications, including decentralized finance (DeFi), tokenized assets, and decentralized identity solutions.
Use cases:
Allowlist Management: In the context of allow list management, Avalanche Network Identity Verification provides an enhanced level of control by requiring users to verify their identity through their web3 accounts. By integrating with existing Web3 profiles, this system fortifies allow list protocols, making it more challenging for unauthorized entities to gain access and ensuring a secure and meticulously managed user allow list.
Bot Prevention:Avalanche Network Identity Verification adds an extra layer of bot prevention by requiring users to verify their identity through their web3 accounts. This method leverages existing Web3 profiles, making it more challenging for bots to infiltrate systems and ensuring a higher level of user authentication.
-
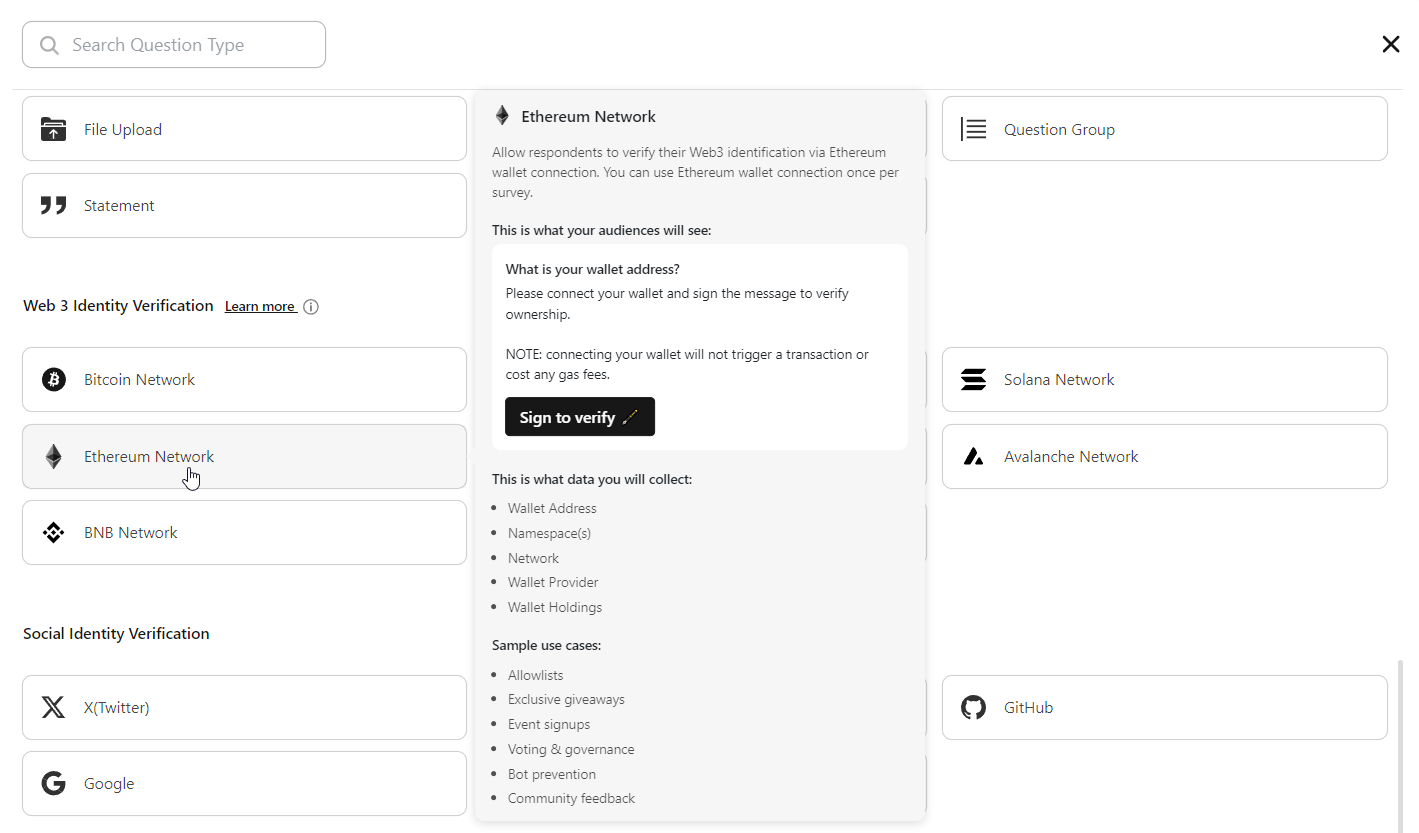
Ethereum Network Identity Identity Verification component and use cases:
Embark on a journey through the Ethereum Network's Identity Verification component, where advanced technology converges with decentralized principles to establish secure user identities.
Use cases:
Voting and Governance Empowerment: Ethereum Identity Verification Network to safeguard the legitimacy and openness of voting and governance procedures. Through the association of user identities with their web3 accounts, this framework forms a secure basis for fostering democratic decision-making within the network, promoting transparency and integrity in the governance processes.
Community Feedback Integration: The Ethereum Identity Verification Network places a high priority on community feedback as an integral part of its development and enhancement strategy. Actively seeking input through surveys, forums, and direct interactions, the network ensures a dynamic and responsive environment.
-
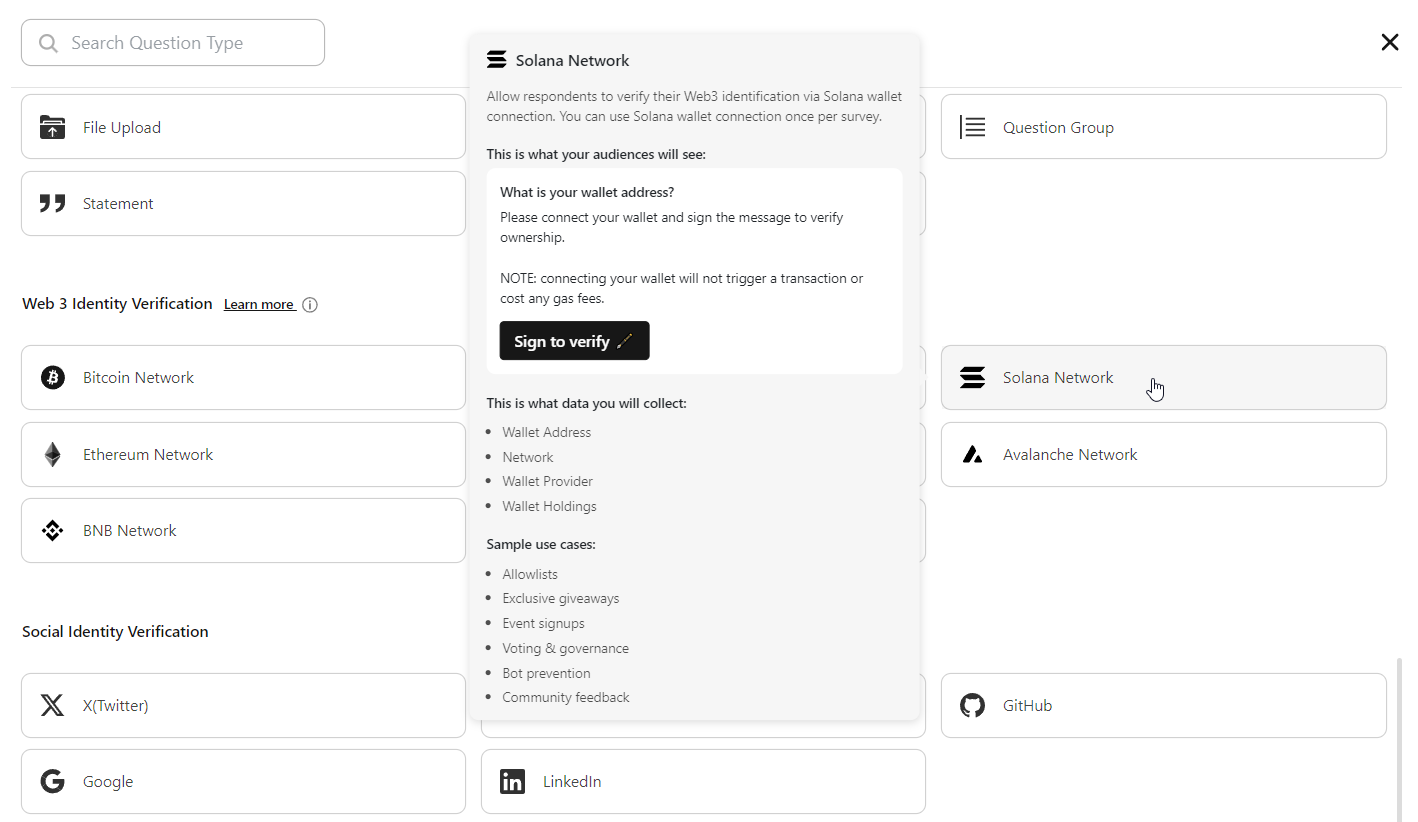
Solana Network Identity Identity Verification component and use cases:
The Solana Network Identity Verification component introduces an advanced layer of security by authenticating user identities through their web3 accounts, bolstering trust and integrity within the Solana ecosystem.
Use cases:
Allowlist Management: In the context of allow list management, Solana Network Identity Verification provides an enhanced level of control by requiring users to verify their identity through their web3 accounts. By integrating with existing Web3 profiles, this system fortifies allow list protocols, making it more challenging for unauthorized entities to gain access and ensuring a secure and meticulously managed user allow list.
Bot Prevention:Solana Network Identity Verification adds an extra layer of bot prevention by requiring users to verify their identity through their web3 accounts. This method leverages existing Web3 profiles, making it more challenging for bots to infiltrate systems and ensuring a higher level of user authentication.
-
Cello Network Identity Identity Verification component and use cases:
The Cello Network Identity Verification component plays a pivotal role in establishing a secure and reliable framework for confirming user identities within the Cello blockchain ecosystem.
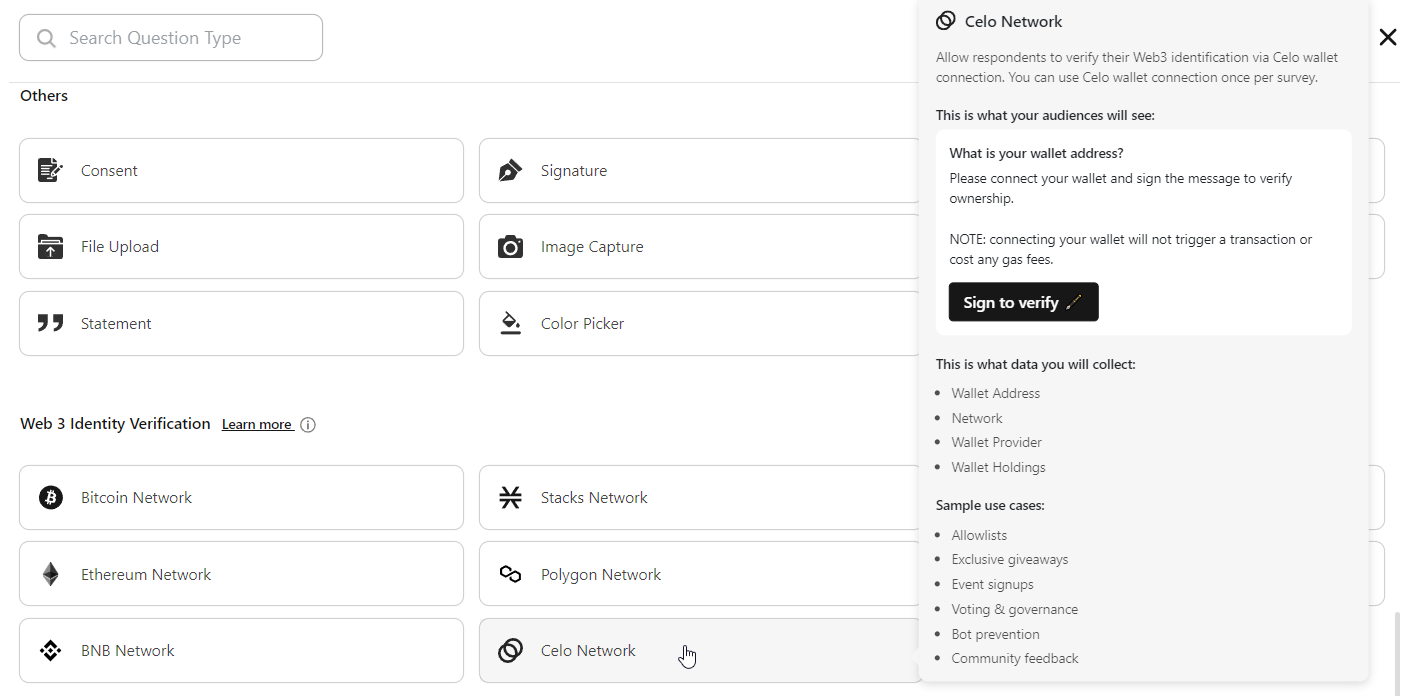
Use cases:
Event Signup Security: Cello Network Identity Verification introduces an additional layer of security for event signups by prompting users to authenticate their identity through their Cello web3 accounts. This approach utilizes established Web3 profiles, heightening the resistance against automated scripts, thereby enhancing the integrity of event signups and ensuring a more authentic and reliable registration process.
Allowlist Management: For allowlist management, Cello Network Identity Verification offers heightened control by mandating users to verify their identity through their web3 accounts. Through seamless integration with established Web3 profiles, this system reinforces allowlist protocols, bolstering security measures against unauthorized access and ensuring a meticulously managed and secure user allowlist.
-
Polygon Network Identity Identity Verification component and use cases:
The Polygon Network Identity Verification component stands at the forefront of security, verifying user identities through web3 accounts and ensuring a robust and trustworthy environment within the Polygon ecosystem.
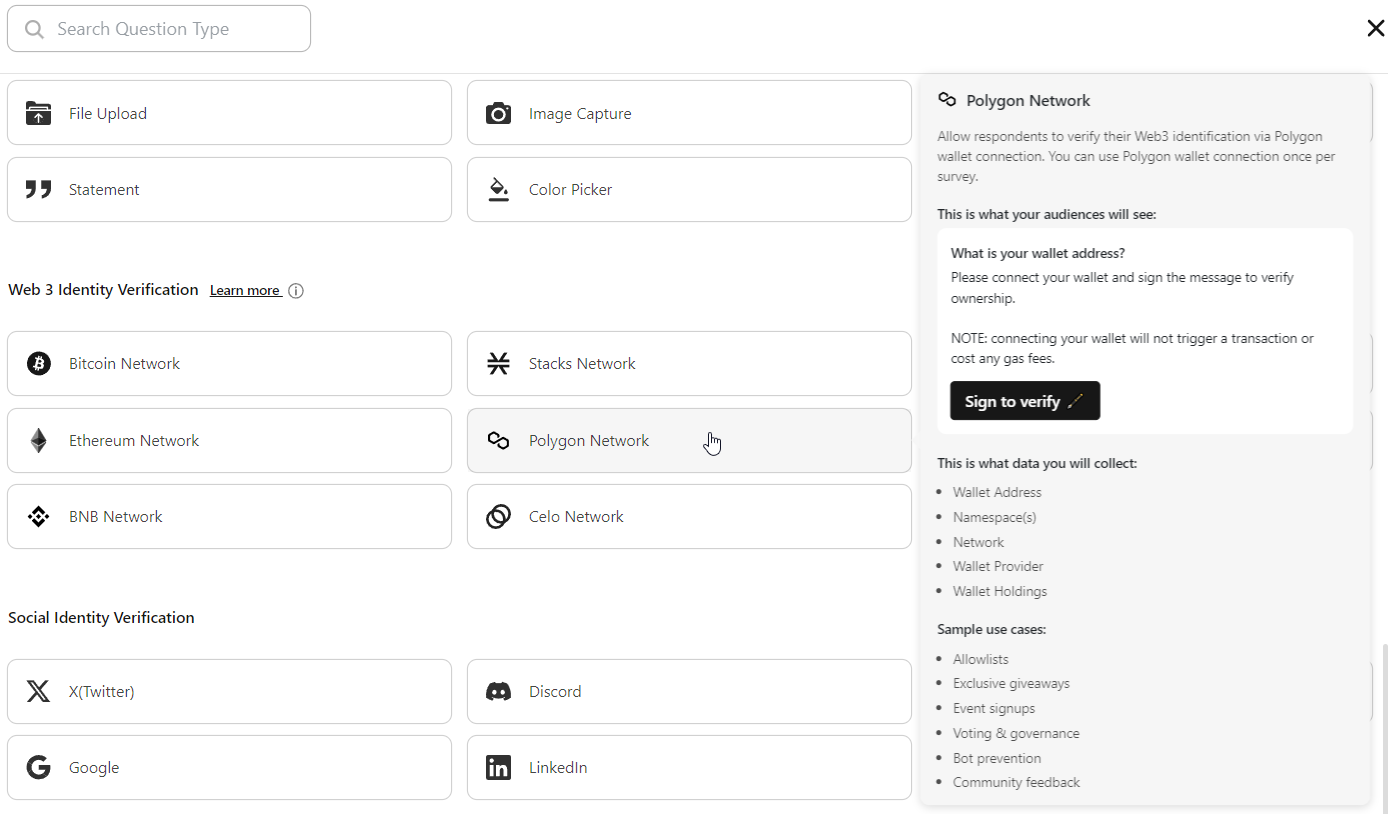
Use cases:
Allowlist Management: In the context of allow list management, Polygon Network Identity Verification provides an enhanced level of control by requiring users to verify their identity through their web3 accounts. By integrating with existing Web3 profiles, this system fortifies allow list protocols, making it more challenging for unauthorized entities to gain access and ensuring a secure and meticulously managed user allow list.
Bot Prevention:Polygon Network Identity Verification adds an extra layer of bot prevention by requiring users to verify their identity through their web3 accounts. This method leverages existing Web3 profiles, making it more challenging for bots to infiltrate systems and ensuring a higher level of user authentication.
What are some Use Cases of Web 3 / Crypto Wallet Address Collection
- NFT Whitelisting: While preparing for your presale, you need a validated list of addresses from your audience. As you build a whitelist through collab, partnerships, and outreach, use BlockSurvey to collect verified wallet addresses. Ensure that only genuine users with verified identities can participate in minting or purchasing NFTs. This prevents fraudulent activities, ensures fairness, and streamlines the onboarding process by reducing the need for manual verification. Try our NFT Whitelist Form for collecting Wallet Addresses. What's more, you can also token gate your whitelist? Read more here.
- Decentralized Finance (DeFi) Platforms: DeFi platforms can also build verified lists for airdrops, presale, and sale of tokens. By integrating BlockSurvey into their end-to-end data collection process, DeFi platforms can collect and track active Web 3 participants from their ecosystem, further opening up opportunities to identify and incentivize active users.
- Initial Coin Offerings (ICOs) and Token Sales: Similar to NFT whitelisting, identity verification can be employed during ICOs and token sales using Web3 wallets in forms and surveys. This ensures that only verified participants can contribute to the project, reducing the risk of fraud and regulatory issues while streamlining the participation process. We have built a Token KYC form for you to integrate and verify customers' identity information seamlessly.
- Airdrops: Web 3.0 wallets can be used to verify the identity of users participating in airdrops through forms and surveys. This ensures that only genuine users receive the airdropped tokens or assets, preventing potential fraud and abuse. By integrating BlockSurvey into the airdrop registration process, project teams can also better target their audience and gather more accurate user data. Here is a sample NFT Airdrop form.
- Secure Voting and Governance: BlockSurvey supports collecting data through forms & surveys for Web 3.0 companies. Similarly, to facilitate secure and transparent on-chain voting, we have an open-source tool called Ballot. Users can cast their votes using their unique wallet address, ensuring that votes are tamper-proof and accurately represent the community's preferences. Feel free to give it a try. It is free.
- Allow List Management: By integrating BlockSurvey into forms and surveys, Web 3 businesses can effectively manage to allow lists for various events or campaigns. This ensures that only verified and authenticated users can access specific content, participate in events, or benefit from exclusive promotions.
Benefits of Verified Wallet Addresses for Web 3 Companies:
- Reduced Fraud: Identity verification using Web 3.0 wallets helps combat fraud by ensuring that users are who they claim to be. This protects both businesses and users from scams, phishing attacks, and other malicious activities that happen from time to time in the crypto space.
- Simplified User Onboarding: Collecting Web 3.0 addresses in a crypto-native way to create a seamless user onboarding and experience for Web 3 natives. This offers reduced drop-off rates, and abandonment thus leading to higher engagement.
Conclusion
Using BlockSurvey in your Web 3.0 data collection through forms & surveys, create a Web 3.0-focused experience, with enhanced security, privacy, and user experience. BlockSurvey is quickly becoming an essential component of data collection for Web 3 companies. Companies and projects working on NFTs, DeFi, and DAOs, have already started seeing the advantages of verified Web 3.0 wallet address collection. If you haven't given it a try, give it a shot today. It's free to get started.
How to Collect Verified Crypto Wallet Addresses for Whitelists, Allowlists, Waitlists, and Airdrops FAQ
What are verified crypto wallet addresses?
Verified crypto wallet addresses are unique identifiers that have been authenticated and validated, ensuring that they belong to the individual or entity claiming ownership.
How are crypto wallet addresses used for a whitelist?
For a whitelist, validated wallet addresses are collected and only those on the whitelist are allowed to participate in specific events or transactions, enhancing security.
How does using verified wallet addresses enhance security?
Using verified wallet addresses ensures that transactions are made with the correct individuals, reducing the risk of fraud or theft.
Get insights.
Unlock value.
- Free plan, no time limit
- Set up in minutes
- No credit card required



